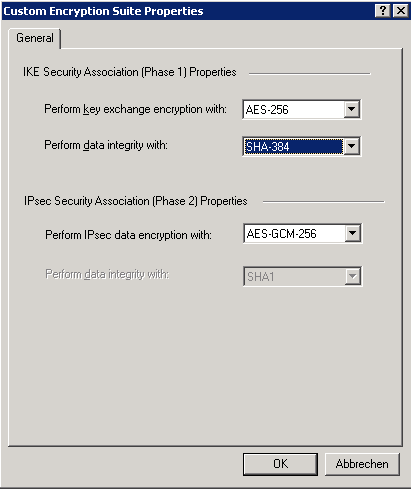
Click Save Configure the condition as follows Email contains a number of matches for the keywords in the selected lists; JSS Ciphers Supported Server Cipher (s) Preferred TLSv12 128 bits ECDHERSAAES128GCMSH56 Curve P256 DHE 256 Accepted TLSv12 256 bits ECDHERSAAES256GCMSHA384 Curve P256 DHE 256 Accepted TLSv12 128 bits ECDHERSAAES128SHA Curve P256 DHE 256 Accepted TLSv12 128 bits ECDHERSAAES128SH56 Curve P256 DHE 256Yes, it is possible to use a Bareos 1 client, but some changes need to be done in the configuration It is possible to use the Bareos 1 client with a Bareos 172 Server However, the new immediate TLS Protocol and TLSPSK are not usable, as the server components do not support it This also means that it is not possible to use TLS with

Out Of Sight Out Of Mind With Security That S Out Of Your Mind
Tls_dhe_rsa_with_aes_256_cbc_sha
Tls_dhe_rsa_with_aes_256_cbc_sha- I found that the downloaded image was not my host binary, rather it is a dynamic HTML page (index?) that OpenSSL generates I printed the contents of SPI flash and you can see it in my terminal output below In fact, the behavior is the same whether or not the host binary is actually present on the OpenSSL serverWeak DHERSADESCBC3SHA Recommended DHEDSSAES128GCMSH56 Weak PSKCHACH0POLY1305 Insecure ADHAES256SH56 Weak ECDHEECDSAAES128SH56 Weak ECDHEECDSACAMELLI56SHA384 Weak SRPAES256CBCSHA Insecure ECDHEPSKNULLSHA Weak PSKAES128CCM8




Strong Ssl Security On Nginx Raymii Org
TLS v12 only (Strong) ALL!SSLv2!SSLv3!TLSv1!TLSv11!aNULL!ADH!eNULL!LOW!MEDIUM!EXPHIGH ECDHERSAAES256GCMThe AmbassadorHost will configure basic TLS termination settings in Ambassador Edge Stack If you need more advanced TLS options on a domain, such as setting the minimum TLS version, you can do it in one of the following ways Transport Layer Security (TLS) AmbassadorHost Automatic TLS with ACME ContentsIntroduction and motivationCertificate management on an Arista switchStep 1 Generate the key pairStep 2 Generate the certificate signing requestStep 3 We submit the CSR to the CA and get the signed certificate back Step 4 Create an SSL profile using the certificateStep 5 SSL profile managementStep 6 Activate eAPI access and refer to the previously Continue
The web_set_sockets_option function configures options for sockets on the client machine This function supports socketlevel replay In the Web HTML protocol, it supports both HTMLbased scripts (Mode=HTML) and URLbased scripts (Mode=HTTP modes) web_set_sockets_option has no effect on replay using WinInetCount only unique matches No;Openssl on RHEL6 is originally based on openssl100 but was rebased to openssl101e with RHEL65 This article is part of the Securing Applications Collection Due to the serious flaws uncovered in openssl during the lifetime of RHEL6 you should always use
Cipher suite correspondence table IANA, OpenSSL and GnuTLS use different naming for the same ciphers The table below lists each cipher as well as its corresponding Mozilla Server Side TLS compatibility level Hex Priority IANA GnuTLS NSS OpenSSLSupported SSL / TLS ciphersuites The following key exchanges and ciphersuites are supported in mbed TLS mbed TLS uses the official NIST names for the ciphersuites For reference purposes, the OpenSSL equivalent of the used names are provided as well (based on the OpenSSL website from November 1st 15)PSKAES256CBCSHA Thus I don't believe I have enabled the banned ciphers Details Linux el7x86_64 # 1 SMP Mon Dec 4 UTC 17 x86_64 x86_64 x86_64 GNU/Linux OpenSSL 102kfips nginx v nginx version nginx/1122 openssl ciphers




Kbid Xxx Tls Downgrade Write Ups




Emq X Authentication And Authentication 2 Mqtt Connection Authentication Core Concepts And Configuration Points In Emq X Programmer Sought
1 The SSL/TLS protocols SSL stands for Secure Sockets Layer and was originally created by Netscape SSLv2 and SSLv3 are the 2 versions of this protocolSsl_optionsciphers46 = DHEPSKAES256CBCSHA ssl_optionsciphers47 = AES256SHA ssl_optionsciphers48 = PSKAES256CBCSHA384Pskaes256cbcsha sslv3 kx=psk au=psk enc=aes(256) mac=sha1 ecdhersaaes128gcmsha256 tlsv12 kx=ecdh au=rsa enc=aesgcm(128) mac=aea d ecdheecdsaaes128gcmsha256 tlsv12 kx=ecdh au=ecds a enc=aesgcm(128) mac=aea d ecdhersaaes128sha256 tlsv12 kx=ecdh au=rsa enc=aes(128) mac=sha2 56 ecdheecdsaaes128sha256 tlsv12 kx=ecdh




Configuring Apache Nginx And Openssl For Forward Secrecy Qualys Security Blog




Top 10 Ssl Security Vulnerability And Solution Part 2 Sap Blogs
Cryptography in RHEL8 RHEL8 has a new mechnism to centralise the cryptographic defaults for a machine This is handled by the cryptopolicies package Details of the rationale and update policy can be found in other documents Strong crypto defaults in RHEL8 and deprecations of weak crypto algorithms Systemwide crypto policies in RHEL 8Clone via HTTPS Clone with Git or checkout with SVN using the repository's web addressOci_load_balancer_load_balancer This resource provides the Load Balancer resource in Oracle Cloud Infrastructure Load Balancer service Creates a




Out Of Sight Out Of Mind With Security That S Out Of Your Mind



Www Cisco Com C Zh Cn Support Docs Security Email Security Appliance Ssl Cipher Strength Details Pdf
The following table shows the OpenSSL Encryption Cipher suites that the driver can use if it can negotiate TLS v10, TLS v11, and TLS v12 with the server, with the name of the corresponding cipher suites Pastebincom is the number one paste tool since 02 Pastebin is a website where you can store text online for a set period of timeA PCI Compliance scan has suggested that we disable Apache's MEDIUM and LOW/WEAK strength ciphers for security Can someone tell me how to disable




Nginx Security Server Side Tls Larry的博客 Csdn博客




Flexible Iot Security Middleware For End To End Cloud Fog Communication Sciencedirect
Weak DHEPSKAES256CBCSHA Secure ECDHERSACHACH0POLY1305 Weak PSKAES128GCMSH56 Weak PSKAES256GCMSHA384 Insecure RSAPSKNULLSH56 Weak PSKAES256CCM Secure ECDHERSAAES128GCMSH56 Recommended ECDHEECDSACHACH0POLY1305 Secure DHERSAAES128CCM 1139 AM AESCBC is an encryption algorithm, whereas SHA is a hashing algorithm, they are seperate algorithms AESGCM algorithm performs both encryption and hashing functions without requiring a seperate hashing algorithm, it is the latest Suite B Next Generation algorithm and probably not supported on as ASA 5505Learn how to use cipher suites with a load balancer to determine the security, compatibility, and speed of HTTPS traffic A cipher suite is a logical entity for a set of algorithms, or ciphers, using Transport Layer Security (TLS) to determine the security, compatibility, and speed of HTTPS trafficAll ciphers are associated with at least one version of TLS 10, 11, and 12




Ssl Protocol Structure Download Scientific Diagram




Psk Authentication Emq Docs
From the Add a condition dropdown list, select Content Keyword List Name theCipher Suite Name (OpenSSL) KeyExch Encryption Bits Cipher Suite Name (IANA) 0x00 None Null 0 TLS_NULL_WITH_NULL_NULLConnection TLS Protocol Configuration MySQL supports encrypted connections using the TLSv1 protocol and (as of MySQL 5646) TLSv11 and TLSv12 Protocol support is built in and cannot be configured as is possible in MySQL 57 and higher The protocol chosen for a given connection depends on the negotiation process



Education Emc Com Content Dam Dell Emc Documents En Us 15ks Lad Ssltls Security And Troubleshooting Pdf




Securing Your Apache 2 4 Web Server With Correct Parameters Yuri S Technology Blog
I have come across that GCM, CCM, SH56 and SHA384 Cipher suites are TLS 12 only So TLS handshake can not be performed with lower TLS version using these suites I am trying to figure out sup Check out Sun Providers Also, By default the local_policyjar and US_export_policyjar under jre_home/lib/security/ might not "enable" the cipher suites you want To enable them, replace those two files with the ones found here Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 Download You should not be able to use the cipher Ney asked I am running Ubuntu Server 04 and proftpd 136 and have an issue setting up TLS I have followed the guide in the config file, but I get



2



2
(3) Negotiated encryption PSKAES256CBCSHA (4) In order to handle N concurrent connections on a Unix platform, stunnel requires nfile (ulimit n) to be higher than 2*N, and nproc (ulimit u) to be higher than NValid from Wednesday, 28 March 18, Valid until Friday, 29 March 19, 1000 Certificate Matches Server Hostname yes (amazoncom) Trust Store 'AppleIt can consist of a single cipher suite such as RC4SHA It can represent a list of cipher suites containing a certain algorithm, or cipher suites of a certain type For example SHA1 represents all ciphers suites using the digest algorithm SHA1 and SSLv3 represents all SSL v3 algorithms Lists of cipher suites can be combined in a single



Cipher Suite Practices And Pitfalls Devcentral



Unix Command Openssl Ciphers Unixshadow
1 Answer1 Yes, the order of Apache's SSLCipherSuite indicates the preferred order To quote the link you've provided (emphasis mine), During the TLS handshake, the client presents its cipher suite, and then the server will select the appropriate cipher to use, as dictated by the SSLHonorCipherOrder If off (the default), then the server will Bug # Support for TLSv11 and TLSv12 Submitted 2108 Modified 1356 Reporter Daniël van Eeden (OCA) Email Updates pskaes256cbcsha sslv3 kx=psk au=psk enc=aes(256) mac=sha1 edhrsadescbc3sha sslv3 kx=dh au=rsa enc=3des(168) mac=sha1 edhdssdescbc3sha sslv3 kx=dh au=dss enc=3des(168) mac=sha1 descbc3sha sslv3 kx=rsa au=rsa enc=3des(168) mac=sha1



Applied Crypto Hardening Bettercrypto Org



St Security Authentication And Encryption With Ssl Tls
Issue/Introduction Learn which TLS ciphers, hashes, and cipher suites are supported by Symanteccloud services such as Email Encryptioncloud and Email Securitycloud at the day of publication of this article 2 Although tlsgetCiphers () claims to support pskaes256cbcsha, it appears that support is not actually implemented Someone did submit a pull request implementing PSK several years ago, but it apparently went stale and was never mergedClient communicate ssl record with SslProviderOPENSSL and SslProviderJDK both both success with same cipher In order to support tlsv13,we upgrade netty 4115Final to 4132Final client platform OpenSSL 102j built on



Www Pjm Com Media Etools Jetstream Jetstream Certification And Testing Ashx



Cipher Suite Practices And Pitfalls Devcentral
Accepted Version Cipher List Cipher Suites Cipher Suites (FIPS) TLS v12 only (Strong) TLS v11 TLS v12 TLS v1 TLS v12 SSL v3 TLS v12 SSL v2 TLS v12 (Weak)Email Encryptioncloud Family Opportunistic cipher set ECDHERSAAES256GCMSHA384 ECDHEECDSAAES256GCMSHA384 DHEDSSAES256Introduction Authentication is an important part of most applications MQTT protocol supports username/password authentication Enabling authentication can effectively prevent illegal client connections Authentication in EMQ X Broker means that when a client connects to EMQ X Broker, the server configuration is used to controls the client's




Seven Grades Of Perfect Forward Secrecy




Let S Encrypt From Start To Finish Tuning With Openssl
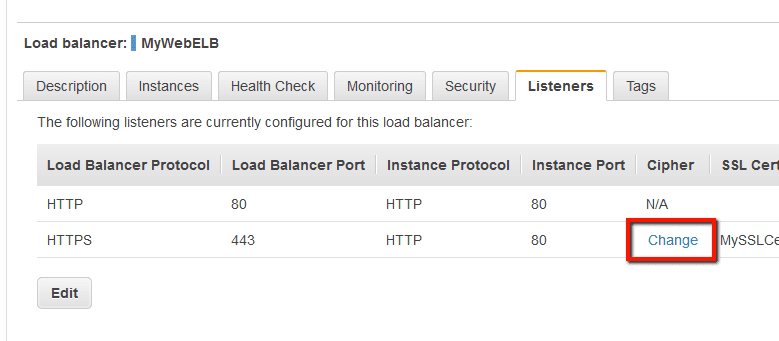
Accepted Version Cipher List Cipher Suite;It can consist of a single cipher suite such as RC4SHA It can represent a list of cipher suites containing a certain algorithm, or cipher suites of a certain type For example SHA1 represents all ciphers suites using the digest algorithm SHA1 and SSLv3 represents all SSL v3 algorithms Lists of cipher suites can be combined in a single Test your application over the Internet with SSLLabs The easiest way to confirm that the load balancer is using the secure ciphers that we chose is to enter the URL of the load balancer in the form on SSL Labs' SSL Server Test pageIf you do not want the name of your load balancer to be shared publicly on SSLLabscom, select the Do not show the results on the boards



Www Spinifexdragon Com Documents Openssl 1 0 2 Cipher Suite List Pdf



St Security Authentication And Encryption With Ssl Tls
pskaes256cbcsha sslv3 kx=psk au=psk enc=aes(256) mac=sha1 ECDHERSAAES128GCMSH56 TLSv12 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHEECDSAAES128GCMSH56 TLSv12 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEADTLS/SSL Cipher Suites WinSCP supports the following cipher suites with TLS/SSL (used with FTPS, WebDAV and S3) – sorted by preference order To see algorithms supported by your specific version of WinSCP, use /info commandline switch TLS_AES_256_GCM_SHA384 TLS_CHACH0_POLY1305_SH56 TLS_AES_128_GCM_SH56 ECDHE ECDSA AES256



Elb Insecure Ssl Ciphers Trend Micro




How To Find Out Cipher Strength Of Ironport Cisco Community




Psk Authentication Emq Docs
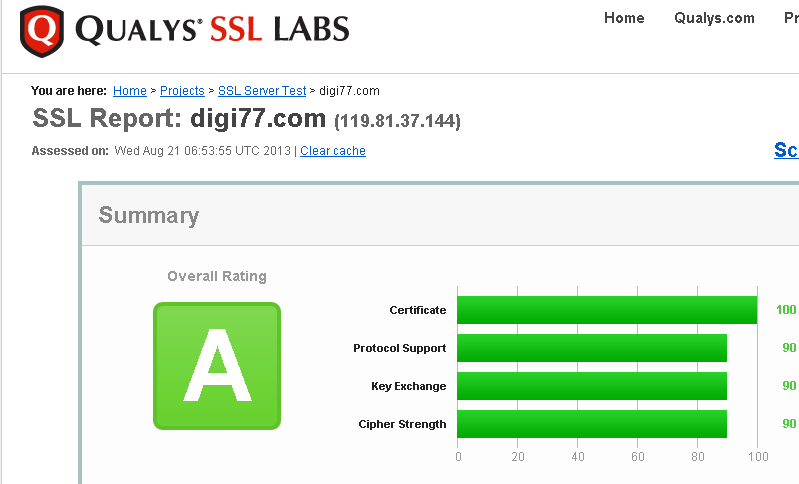



Mitigating The Beast Heartbleed Drown And Poodle Attack Attack On Ssl Tls Grade A Eagle Eye Nonprofit Organization




Kbid Xxx Tls Downgrade Write Ups
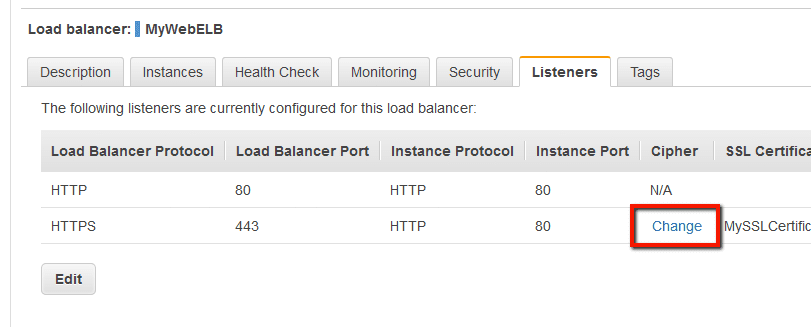



Elb Insecure Ssl Ciphers Trend Micro




Can Firefox Be Forced To Use Ssl Instead Of Tls Stack Overflow



Emq Conf Tls Psk Issue 2311 Emqx Emqx Github
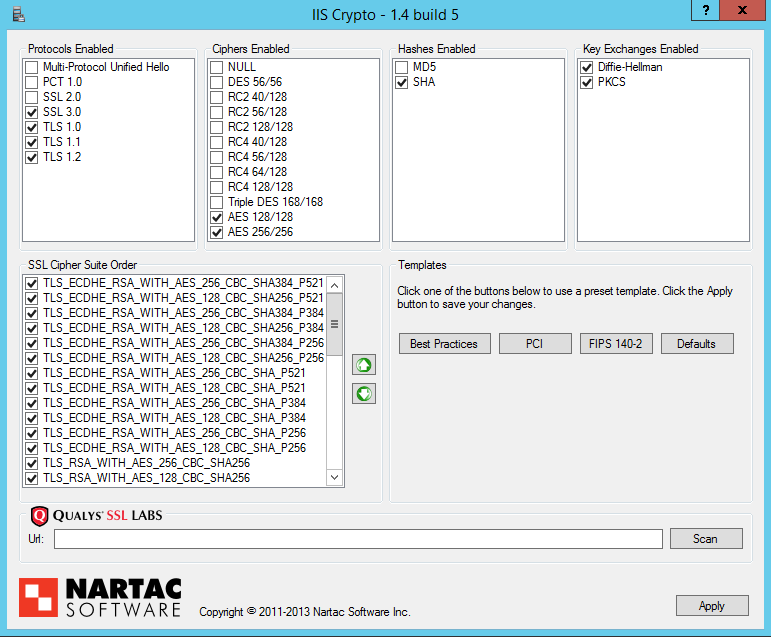



Applied Crypto Hardening Bettercrypto Org




C Wrapper Api Guide December 7th 15 Version Pdf Free Download




Openssl Ciphers Stuff I M Up To




Accepted Ssl Ciphers




Test The Two Way Authentication Between The Browser And Openssl Programmer Sought
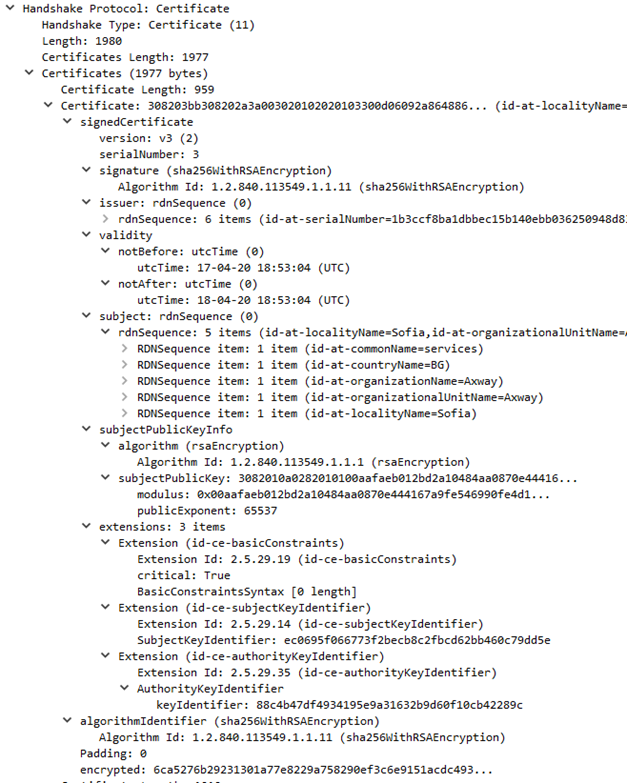



St Security Authentication And Encryption With Ssl Tls
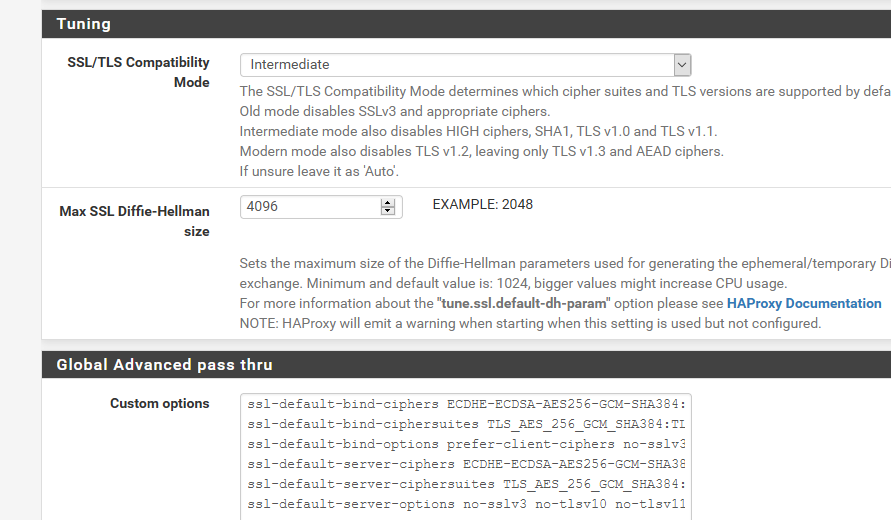



How To Disable Sslv3 With Haproxy Netgate Forum




날으는물고기 Security Server Side Tls Recommended Configurations



Cipher Suite Practices And Pitfalls Devcentral




Rabbitmq Ssl Upgrade Error With Go Client Program




Openldap Tls Cipher Options Linuxadmin
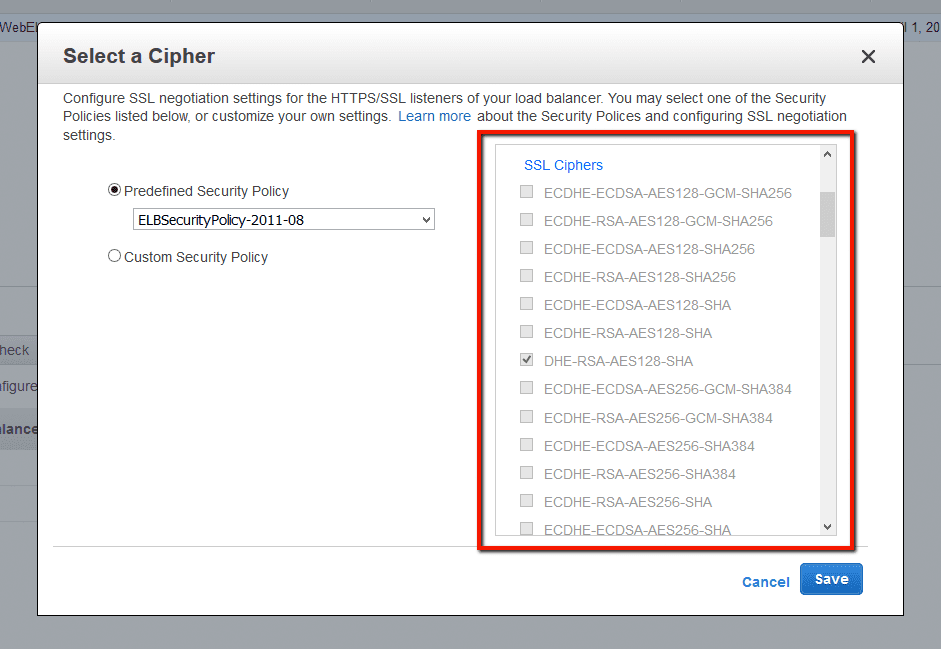



Elb Insecure Ssl Ciphers Trend Micro



Why Is My Server Still Rated With T I Want B
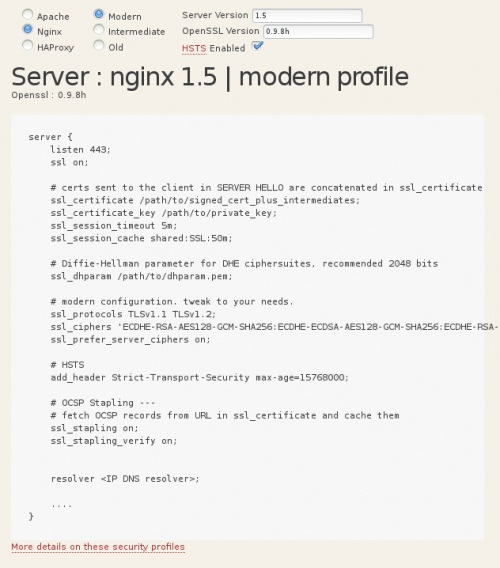



Nginx Security Server Side Tls Larry的博客 Csdn博客




Top 10 Ssl Security Vulnerability And Solution Part 1 Sap Blogs



Support For Tls Psk With Aes 128 Cbc Sha256 Issue 6 Openmobilealliance Oma Lwm2m For Developers Github
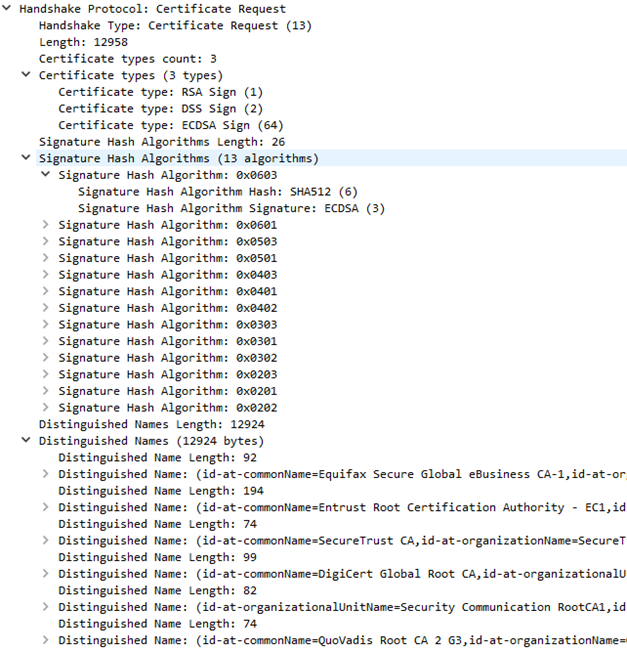



St Security Authentication And Encryption With Ssl Tls




Strong Ssl Security On Nginx Raymii Org



1
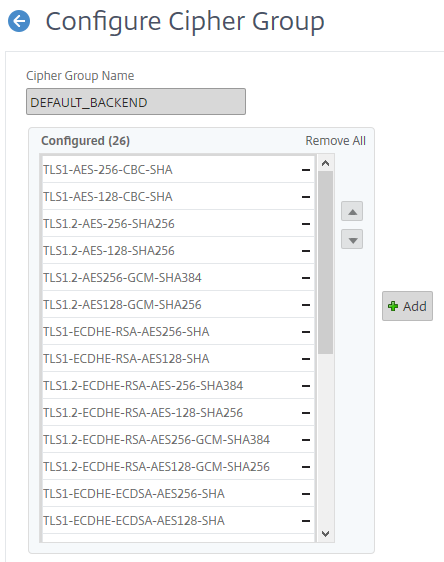



Netscaler Ssl Ciphers Fun With Bitwarden It Randomness



1



Q Tbn And9gcryhifuqtdnvsd5jdvr18vvwizmb2wfmbhscy3fu3o Usqp Cau



2




Kbid Xxx Tls Downgrade Write Ups



Www Silver Peak Com Sites Default Files Userdocs Silver Peak Security Algorithms june17 Pdf




How To Find Out Cipher Strength Of Ironport Cisco Community
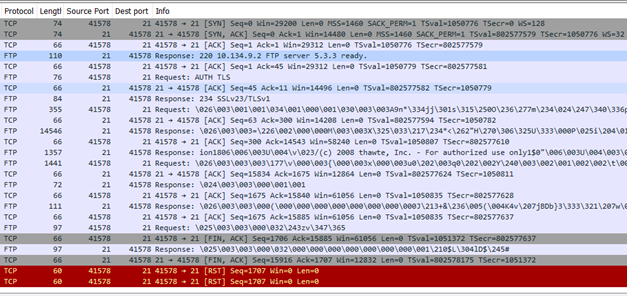



St Security Authentication And Encryption With Ssl Tls



Dd Wrt Forum View Topic New Beta R 09 13 19 R




Aes Encryption Everything You Need To Know About Aes




Psk Authentication Emq Docs



Http Faculty Missouri Edu Calyamp Publications Iot Security Cloudfog Fgcs18 Pdf
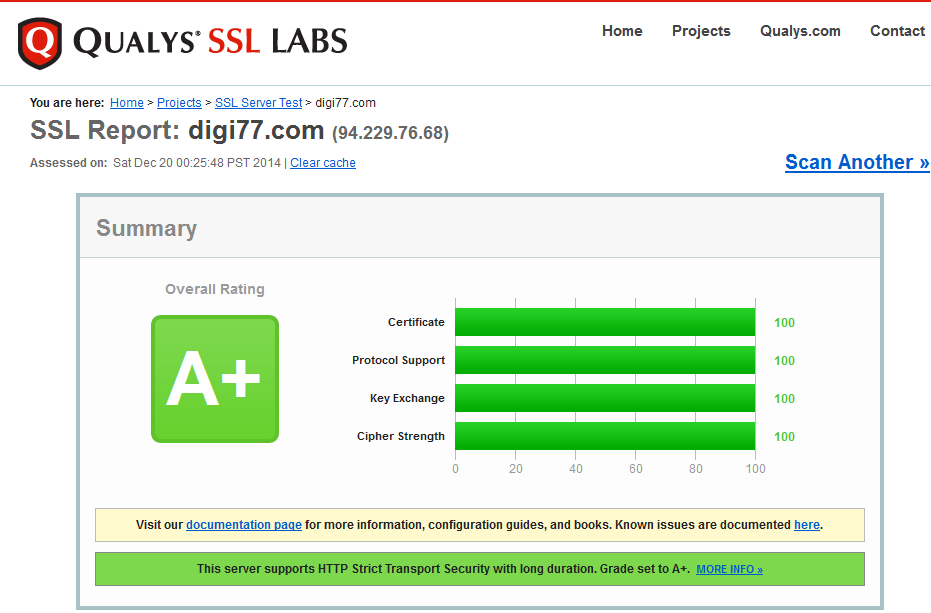



Mitigating The Beast Heartbleed Drown And Poodle Attack Attack On Ssl Tls Grade A Eagle Eye Nonprofit Organization
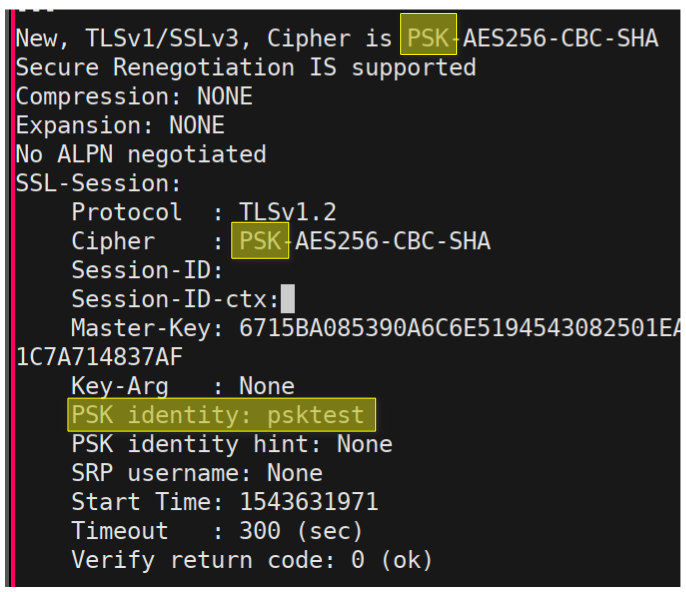



Esp32 Deep Sleep Connecting To Mqtt
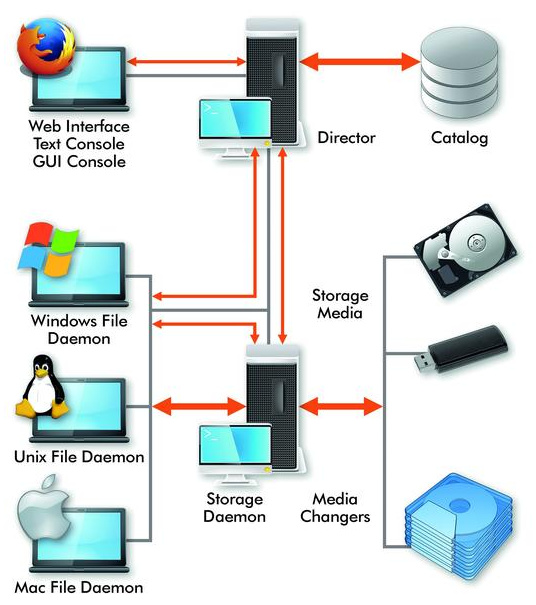



Bareos Backup Archiving Recovery Feature Nethserver Community



Psk Based Tls With Openssl Issue 231 Google Conscrypt Github



2



Education Emc Com Content Dam Dell Emc Documents En Us 15ks Lad Ssltls Security And Troubleshooting Pdf




Pjsip Cipher 256 Asterisk Sip Asterisk Community
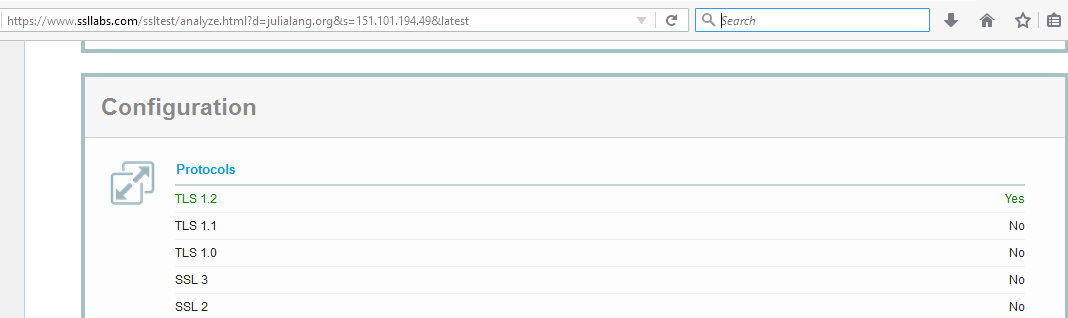



Nss Error Dr John S Tech Talk
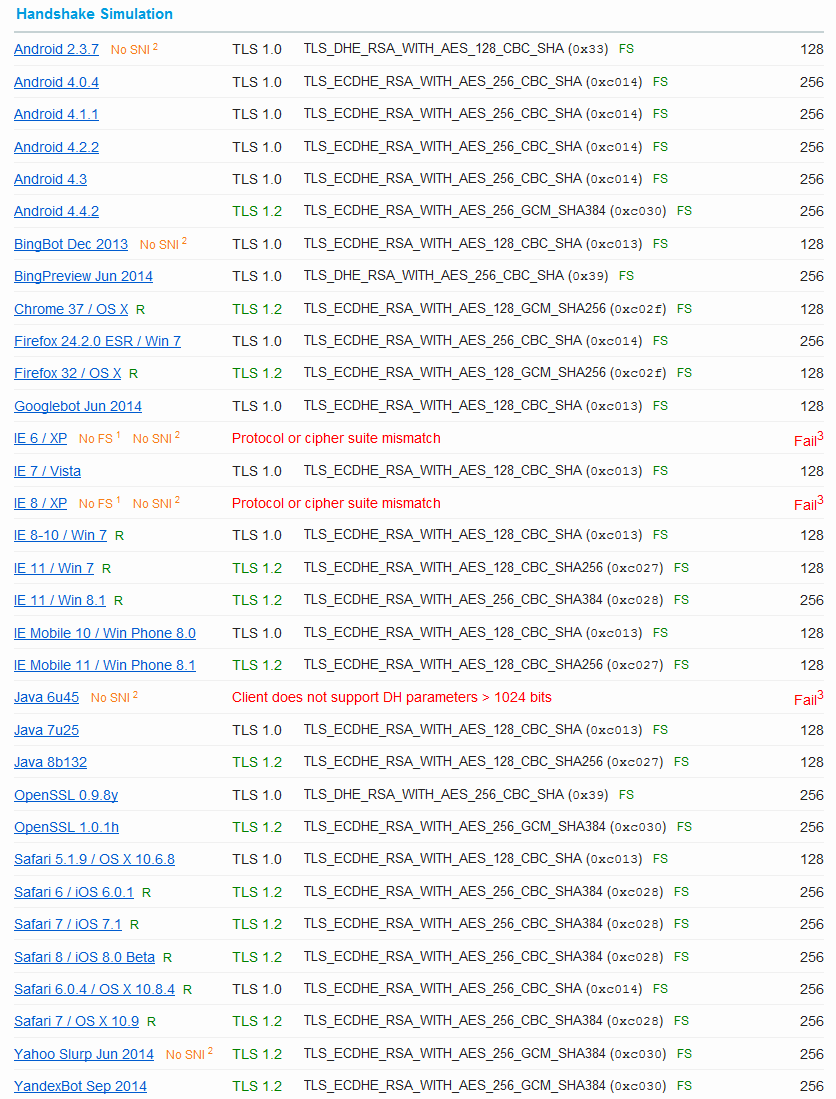



Apache Ssl Cipher Suites Perfect Forward Secrecy Weberblog Net
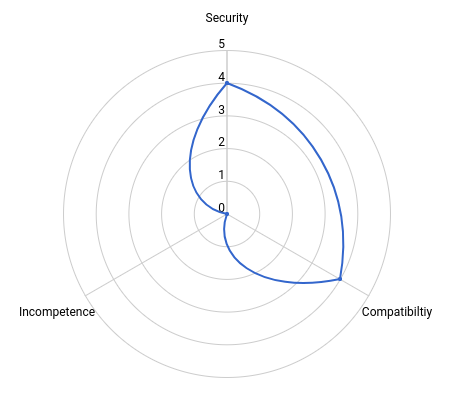



Tls Configuration Cipher Suites And Protocols By David B Templeton Medium




Is The Order Of Cipher Names In Tidserveriohandlersslopenssl Ssloptions Cipherlist Important Stack Overflow




Pdf Guidelines For The Selection Configuration And Use Of Transport Layer Security Tls Implementations Semantic Scholar




Test The Two Way Authentication Between The Browser And Openssl Programmer Sought




Stunnel Performance



Campus Barracuda Com Download Pdf Article 4690



Afk Geek Blog It Tutorials Games And Everything Geek




Ssl Ciphers Internet Lab Ru



Fenix Tecnico Ulisboa Pt Downloadfile Extendedabstract Pdf




Omero Cli Import Error Usage Issues Image Sc Forum




Hp Ilo4 Ssl Circular Reference Help Let S Encrypt Community Support



Campus Barracuda Com Download Pdf Article




Is Not Supported Elliptic Curve Engine



Arc Tls Handshake Fails Issue 2 Unitedstates Inspectors General Github




Openssl Ciphers Stuff I M Up To



Server User Guide Atomjump Messaging



Www W3 Org 14 Strint Papers 05 Pdf




Curl ว ธ หา Ciphers Suites Tls
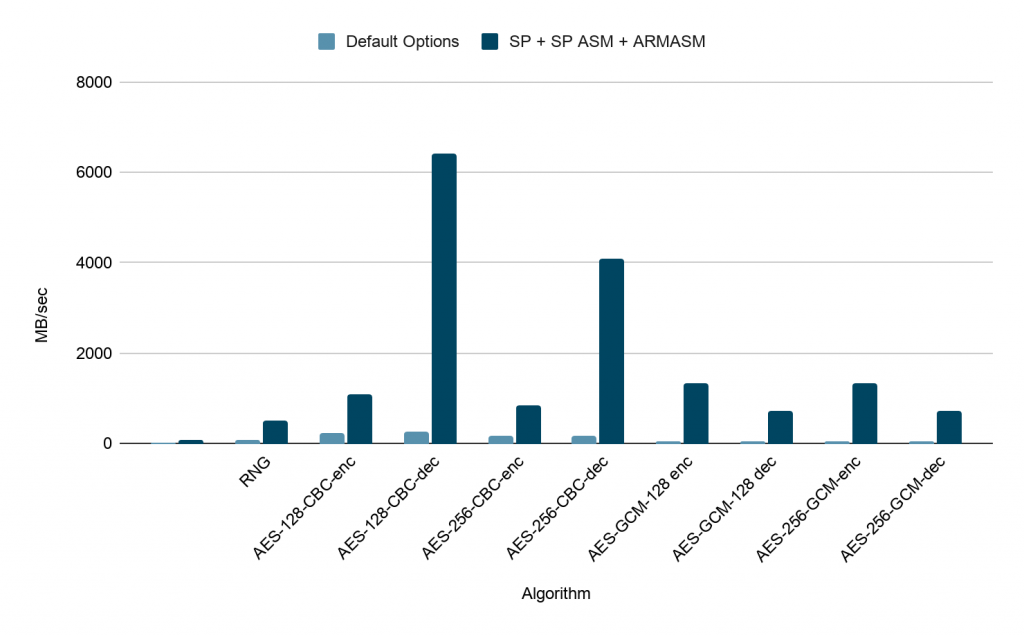



Recent News Wolfssl Embedded Ssl Tls Library




Dtls Aes 256 Cbc With Sha How Do I Calculate The Final Encrypted Handshake Message Stack Overflow
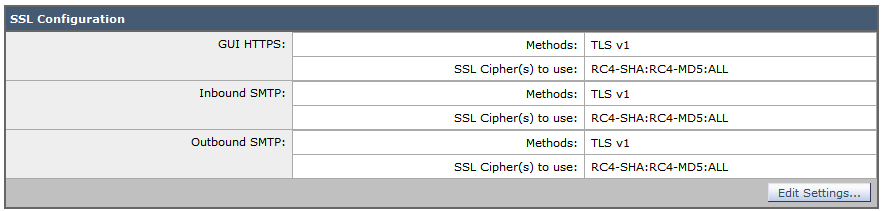



Applied Crypto Hardening Bettercrypto Org




Extreme Access Control Eac Freeradius Default Cipher List Extreme Networks Support Community




How To Control Tls Ciphers In Your Aws Elastic Beanstalk Application By Using Aws Cloudformation Aws Security Blog
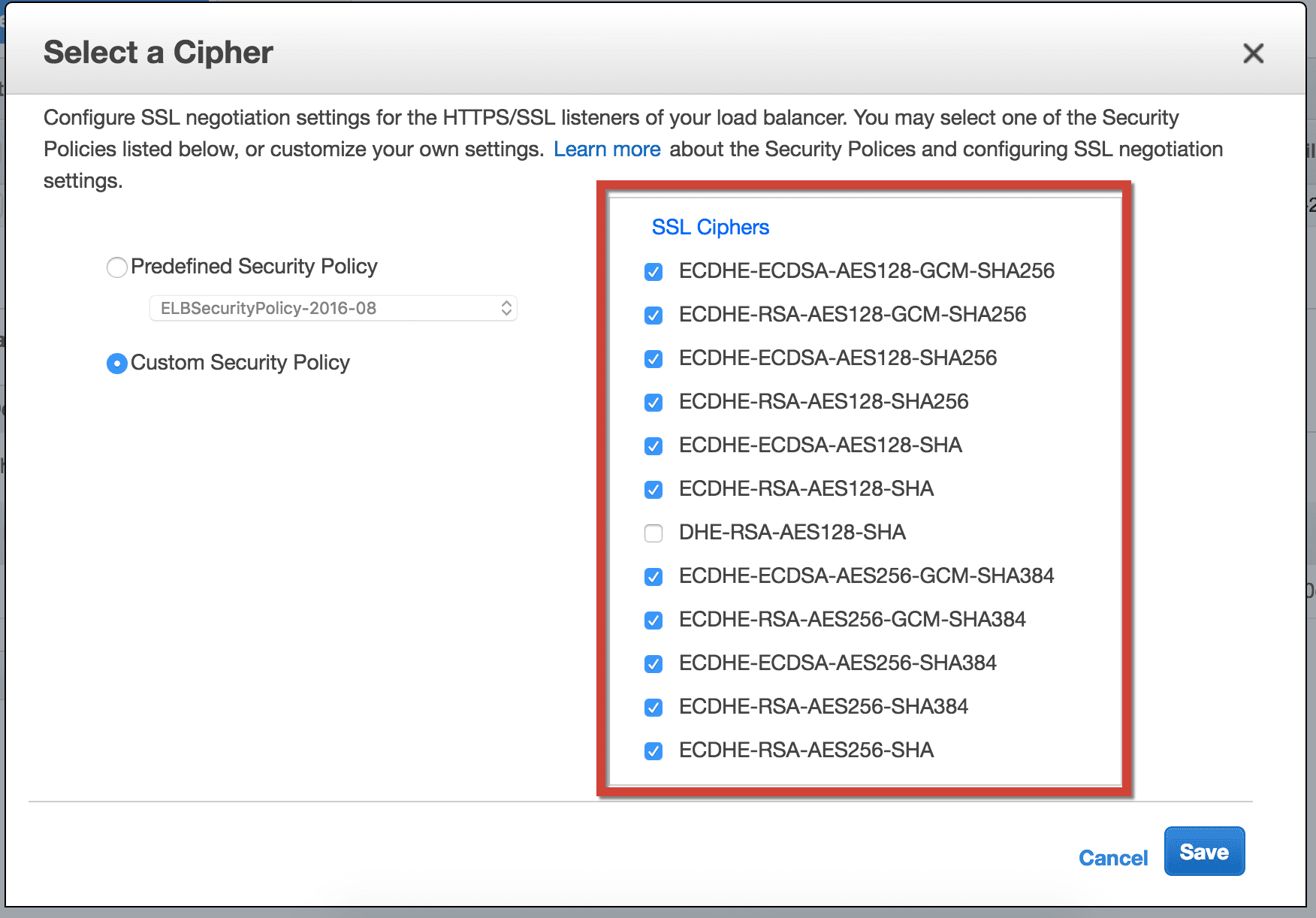



Elb Insecure Ssl Ciphers Trend Micro



2
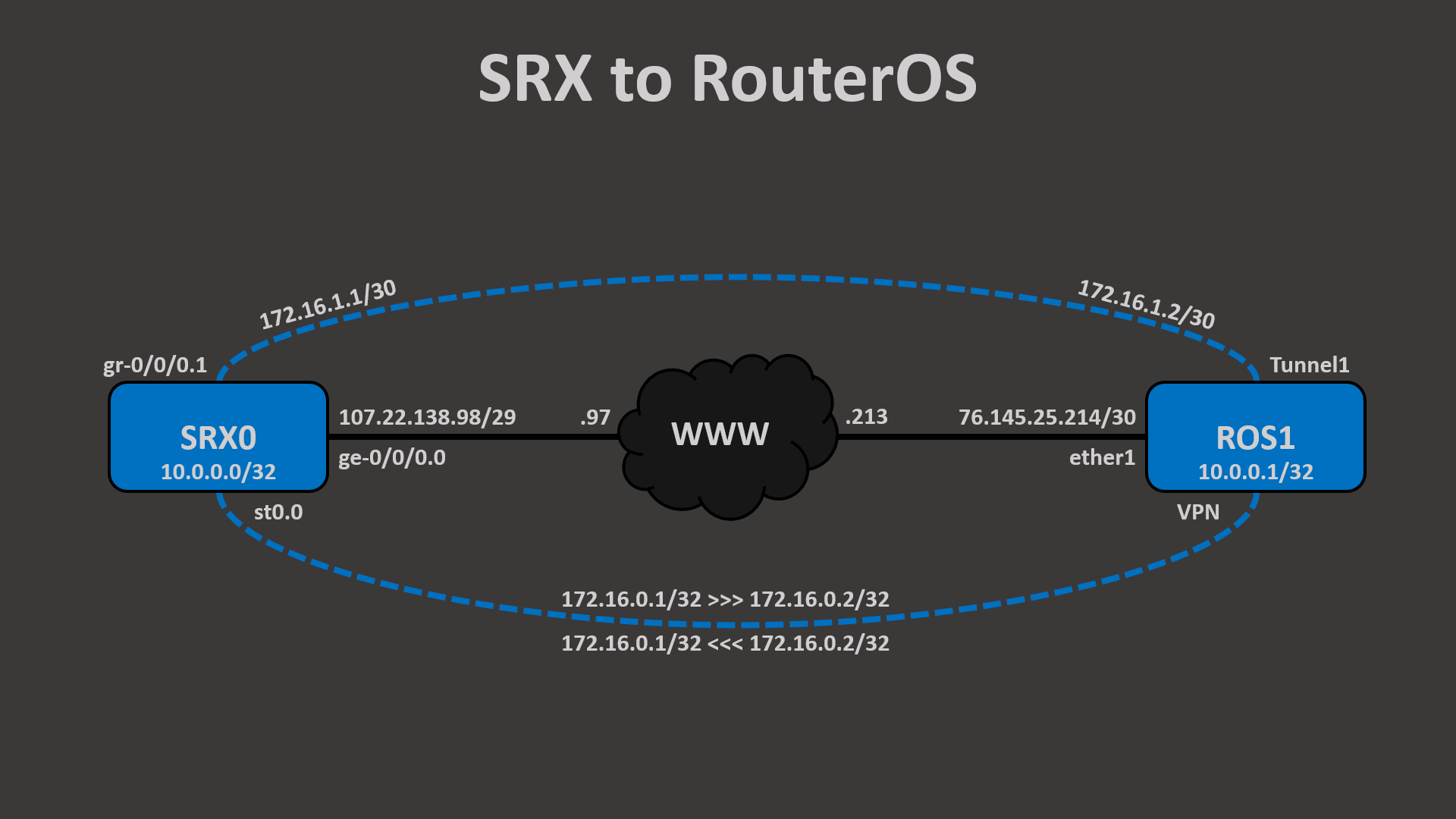



Psk Ipsec Vpn Srx To Routeros Node 9 Tech Blog



2



2
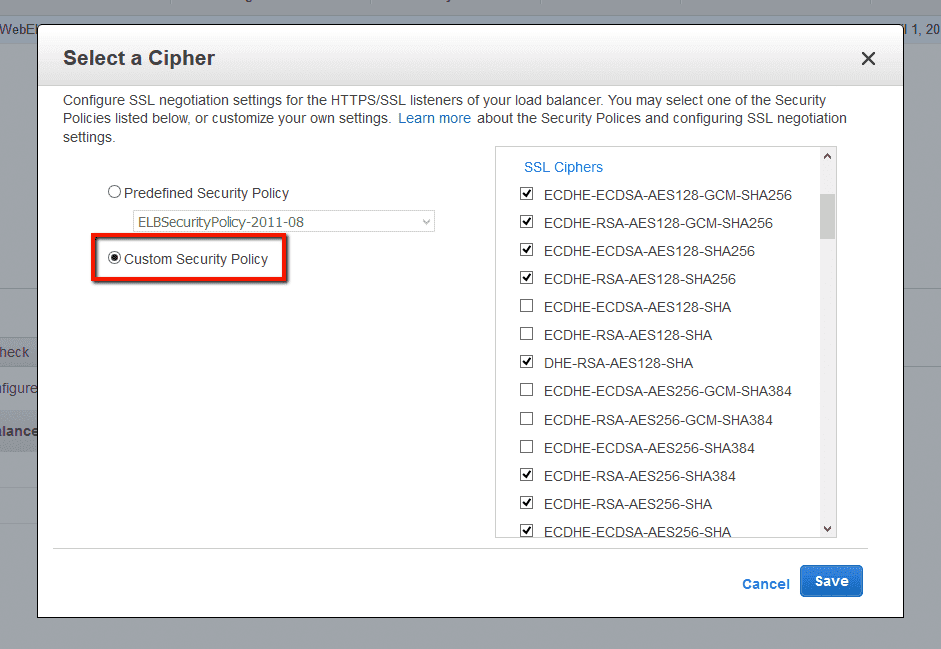



Elb Insecure Ssl Ciphers Trend Micro



Q Tbn And9gctcokk6b69atjd5d9wfxgka1nx6equlkq6gnmxrtrri2 Zqdjqj Usqp Cau



Education Emc Com Content Dam Dell Emc Documents En Us 15ks Lad Ssltls Security And Troubleshooting Pdf



Crypto Tls Available Ciphers List Lacks Aes 256 And Sha 2 Based Combination Issue 94 Golang Go Github


